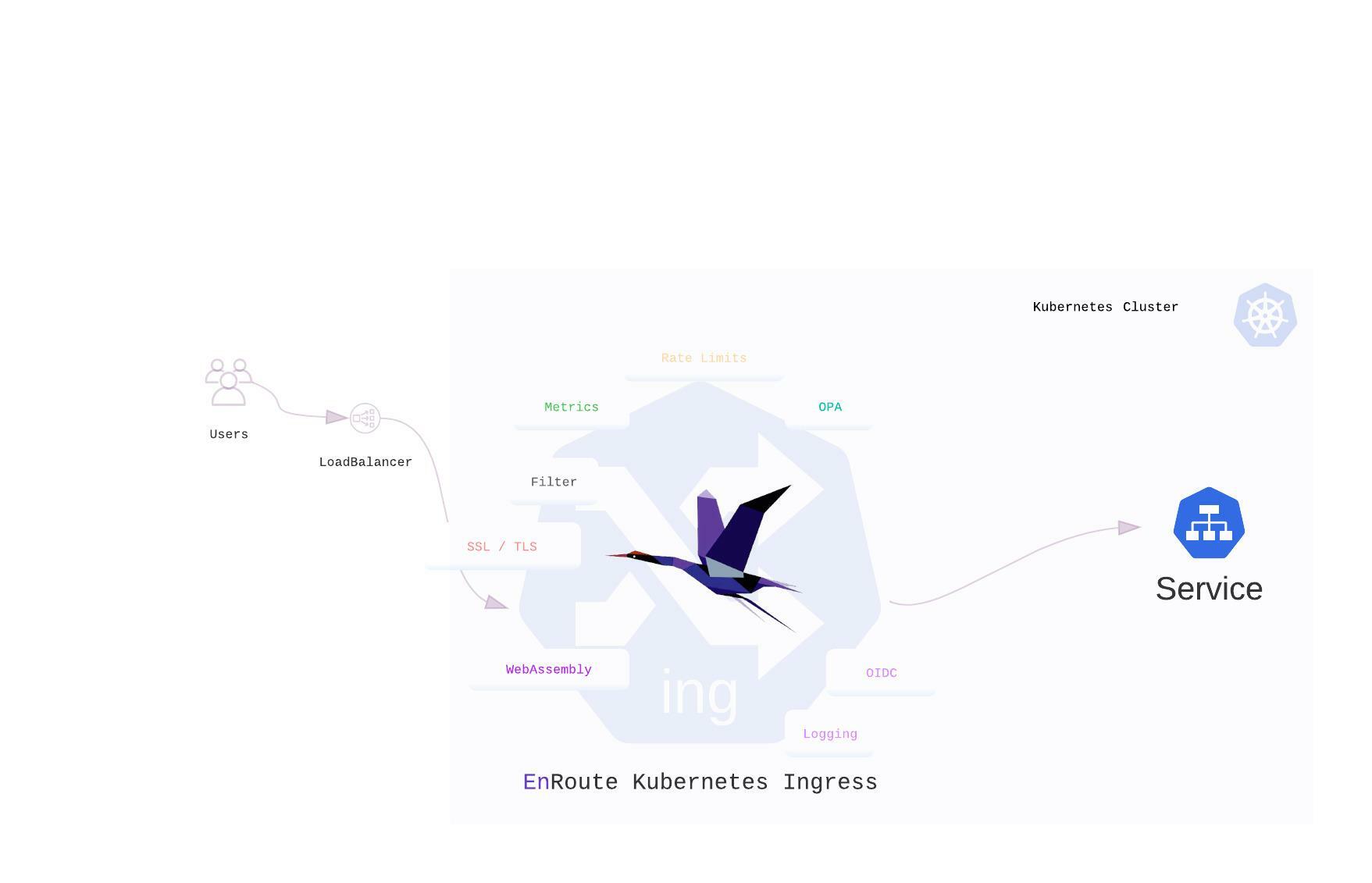
EnRoute Edge Kubernetes Ingress API Gateway
Getting Started with EnRoute Gateway
EnRoute Universal Gateway
EnRoute Universal Gateway is a an API gateway built to support traditional and cloud-native use cases. It is designed to run either as a Kubernetes Ingress Gateway, Standalone Gateway, Horizontally scaling L7 API gateway or a Mesh of Gateways. Depending on the need of the user, the environment, the application, either one or many of these solutions can be deployed.
EnRoute also supports plugins/filters to extend functionality and enforce policies. The features page lists the available plugins for the Gateway. More details about each of the plugins can also be found on plugin pages.
A consistent policy framework across all these network components makes the EnRoute Universal Gateway a versatile and powerful solution.
What this article covers
This article covers how to get started with the EnRoute Kubernetes Ingress Gateway. The minimum requirement is a working Kubernetes cluster.
We first install example workloads and provide connectivity and security for these workloads using EnRoute. EnRoute configuration includes Global Configuration, per-host config and per-route config. EnRoute provides a helm chart to easily configure each of these aspects
EnRoute Helm Charts
EnRoute can be easily configure using helm charts. The following helm charts are available
| Chart | Description |
|---|---|
enroute | Use this chart to configure and install EnRoute Ingress API Gateway |
demo-services | Use this chart to install workloads used to demo EnRoute (eg: httpbin, grpcbin) |
service-globalconfig | Use this chart to configure EnRoute global configuration (eg: Global Rate-Limit Engine Config, Configuration for Mesh Integration, Filters for all traffic - eg: Health Checker, Lua, etc.) |
service-host-route | Use this chart to provide L7 connectivity and policy for a service using a host-and-route (GatewayHost) or just a route (ServiceRoute) |
Configuration Overview
The demo-services helm chart installs service httpbin, grpcbin and echo.
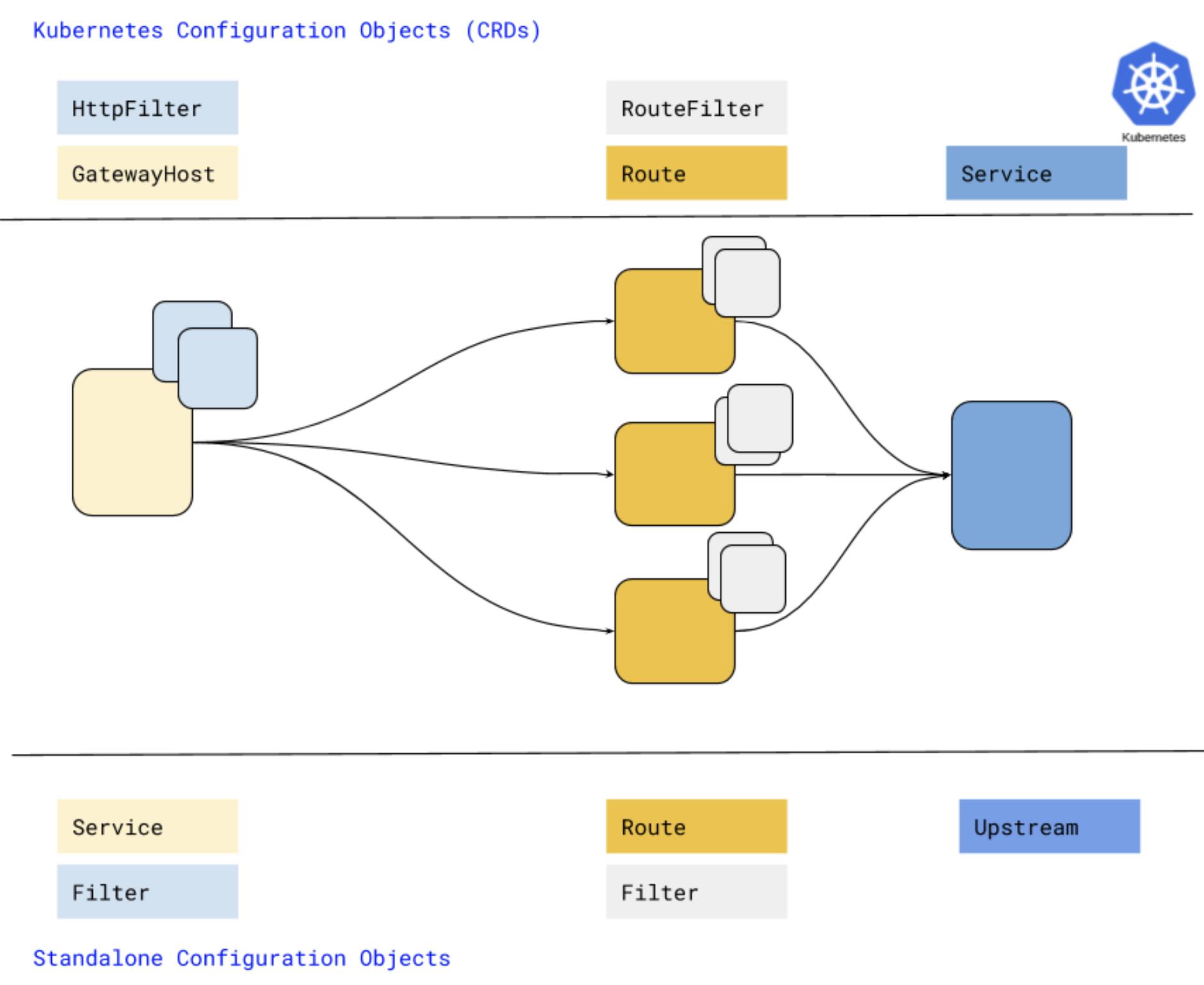
Traffic going to a service needs a host and a route. A host is the root of a configuration tree and with a route defines a way to reach the service. A resource of type GatewayHost can be use to create a Host and a route. A resource of ServiceRoute creates a route to a service while attaching that route to an existing host.
Below we show a list of configuration items we create to make these services externally accessible
| Service | Host | Route | Resource | Notes |
|---|---|---|---|---|
httpbin | * | / | GatewayHost | Create a Host and a Route |
echo | * | /echo | ServiceRoute | Create a Route for echo that gets associated to Host created in previous step |
grpcbin | grpcbin.enroutedemo.com | / | GatewayHost | Create a Host and Route |
We add a GatewayHost that includes a host (fqdn *) and route / to make service httpbin externally accessible.
Next, a ServiceRoute for route /echo maps the service echo to the host created in earlier step (fqdn *)
Next, another GatewayHost for route / maps the service grpcbin to host (fqdn grpcbin.enroutedemo.com) and route /
We will go through the following steps
Add EnRoute helm repo
Add the helm chart -
helm repo add saaras https://charts.getenroute.io
Check repositories -
helm search repo
NAME CHART VERSION APP VERSION DESCRIPTION
saaras/demo-services 0.1.0 0.1.0 Demo Workloads - httpbin, echo, grpcbin
saaras/enroute 0.7.0 v0.11.0 EnRoute API Gateway
saaras/service-globalconfig 0.2.0 v0.11.0 Global Config and Global Filters for EnRoute
saaras/service-host-route 0.2.0 v0.11.0 Host (GatewayHost), Route (ServiceRoute) co...
saaras/service-policy 0.5.0 v0.11.0 Demo Service L7 Policy using EnRoute API Gateway
Install EnRoute
helm install enroute-demo saaras/enroute \
--set serviceAccount.create=true \
--create-namespace \
--namespace enroutedemo
NAME: enroute-demo
LAST DEPLOYED: Mon Jul 25 21:53:15 2022
NAMESPACE: enroutedemo
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
𝙴𝚗𝚁𝚘𝚞𝚝𝚎 Ingress API Gateway Community Edition Installed!
-------------------------------------------------------
Request a free evaluation license for enterprise version
by sending an email to contact@saaras.io
Slack Channel - https://slack.saaras.io
Getting Started Guide - https://getenroute.io/docs/getting-started-enroute-ingress-controller/
EnRoute Features - https://getenroute.io/features/
kubectl get all -n enroutedemo
NAME READY STATUS RESTARTS AGE
pod/enroute-demo-5b4d45ff6c-mzv4b 3/3 Running 0 16m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/enroute-demo LoadBalancer 10.43.91.42 212.2.242.227 80:30808/TCP,443:31920/TCP 16m
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/enroute-demo 1/1 1 1 16m
NAME DESIRED CURRENT READY AGE
replicaset.apps/enroute-demo-5b4d45ff6c 1 1 1 16m
Install Demo Services
kubectl create namespace echo
kubectl create namespace httpbin
kubectl create namespace grpc
kubectl create namespace avote
kubectl create namespace udpserver
helm install demo-services saaras/demo-services
kubectl get svc --all-namespaces
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
default kubernetes ClusterIP 10.43.0.1 <none> 443/TCP 2d21h
kube-system kube-dns ClusterIP 10.43.0.10 <none> 53/UDP,53/TCP,9153/TCP 2d21h
enroutedemo enroute-demo LoadBalancer 10.43.91.42 212.2.242.227 80:30808/TCP,443:31920/TCP 16m
echo echo ClusterIP 10.43.137.85 <none> 9001/TCP 21s
httpbin httpbin ClusterIP 10.43.104.4 <none> 9000/TCP 21s
grpc grpcbin ClusterIP 10.43.56.47 <none> 9002/TCP 21s
However we still need to program EnRoute to expose a service.
Create GatewayHost for service httpbin
helm install httpbin-host saaras/service-host-route \
--namespace=httpbin \
--set service.name=httpbin \
--set service.prefix=/ \
--set service.port=9000
Note the public-IP of EnRoute LoadBalancer type of service, we can use this IP address to send test traffic
curl 212.2.242.227/get
{
"args": {},
"headers": {
"Host": "212.2.242.227",
"User-Agent": "curl/7.68.0",
"X-Envoy-Expected-Rq-Timeout-Ms": "15000",
"X-Envoy-Internal": "true"
},
"origin": "10.42.1.1",
"url": "http://212.2.242.227/get"
}
kubectl describe \
-n httpbin gatewayhosts.enroute.saaras.io \
httpbin-9000-gatewayhost-httpbin-host
Name: httpbin-9000-gatewayhost-httpbin-host
Namespace: httpbin
Labels: app=httpbin
app.kubernetes.io/managed-by=Helm
Annotations: meta.helm.sh/release-name: httpbin-host
meta.helm.sh/release-namespace: httpbin
API Version: enroute.saaras.io/v1
Kind: GatewayHost
Metadata:
...
Spec:
Routes:
Conditions:
Prefix: /
Services:
Name: httpbin
Port: 9000
Virtualhost:
Fqdn: *
Events: <none>
Create ServiceRoute for service echo
helm install echo-route saaras/service-host-route --namespace=echo --set service.name=echo --set service.port=9001 --set routeonly=true --set service.prefix=/echo
NAME: echo-route
LAST DEPLOYED: Mon Jul 25 22:38:15 2022
NAMESPACE: echo
STATUS: deployed
REVISION: 1
TEST SUITE: None
kubectl describe -n echo serviceroutes.enroute.saaras.io echo-9001-serviceroute-echo-route
Name: echo-9001-serviceroute-echo-route
Namespace: echo
Labels: app=echo
app.kubernetes.io/managed-by=Helm
Annotations: meta.helm.sh/release-name: echo-route
meta.helm.sh/release-namespace: echo
API Version: enroute.saaras.io/v1
Kind: ServiceRoute
Metadata:
...
Spec:
Fqdn: *
Route:
Conditions:
Prefix: /echo
Services:
Name: echo
Port: 9001
Events: <none>
curl 212.2.242.227/echo
User-Agent: curl/7.81.0
X-Envoy-Expected-Rq-Timeout-Ms: 15000
X-Envoy-Internal: true
X-Forwarded-For: 192.168.115.133
X-Forwarded-Proto: http
X-Request-Id: b78c2cd5-a321-41f0-b0ee-43c9572be09f
X-Request-Start: t=1721280851.962
Create GatewayHost for service grpcbin
helm install grpcbin-host saaras/service-host-route –namespace=grpc –set service.name=grpcbin –set service.prefix=/ –set service.port=9002 –set service.fqdn=grpcbin.enroutedemo.com –set service.protocol=h2c
Setup DNS to point to external IP of EnRoute LoadBalancer service and send test traffic
./go/bin/grpcurl -v -plaintext grpcbin.enroutedemo.com:80 hello.HelloService.SayHello
Resolved method descriptor:
rpc SayHello ( .hello.HelloRequest ) returns ( .hello.HelloResponse );
Request metadata to send:
(empty)
Response headers received:
content-type: application/grpc
date: Mon, 25 Jul 2022 23:12:24 GMT
server: envoy
x-envoy-upstream-service-time: 2
Response contents:
{
"reply": "hello noname"
}
Response trailers received:
(empty)
Sent 0 requests and received 1 response
Use the External IP to send traffic
The EnRoute service can be reached using the External-IP and a request on path /get sends it to the httpbin service
curl 212.2.246.47/get
{
"args": {},
"headers": {
"Host": "212.2.246.47",
"User-Agent": "curl/7.68.0",
"X-Envoy-Expected-Rq-Timeout-Ms": "15000",
"X-Envoy-Internal": "true"
},
"origin": "10.42.0.41",
"url": "http://212.2.246.47/get"
}
Understanding EnRoute configuration setup in previous step
The above steps create the following routing rules -
GatewayHost (```*```) +---> Route (/) -> Service (httpbin)
+---> Route (/echo) -> Service (echo)
GatewayHost (grpcbin.enroutedemo.com) -> Route (/) -> Service (grpcbin)
Note that the route for services httpbin and grpcbin is setup using GatewayHost and the route for service echo is setup using ServiceRoute type of resource
EnRoute Config Model across Kubernetes Ingress Gateway and Standalone Gateway
EnRoute can be used to protect services outside kubernetes using the standalone gateway or services running inside kubernetes.
EnRoute follows a configuration model similar to Envoy and is extensible using Filters. It uses filters to extend functionality at the global Service level and per-route level. The config objects used for this are - GatewayHost, Route, HttpFilter, RouteFilter and Service as shown here for Kubernetes gateway.
Regardless of where the workload runs, a consistent service policy can be defined once and applied to secure any service running inside or without Kubernetes using Envoy.
EnRoute provides key functionality using modular filters which make it easy to secure any service.